Update:
Worked for a little over 48 hours. Then it went back to MSEdgeHTM. To fix this I set a scheduled task to run every hour to re-apply the DefaultAssociations.xml file.
The action is dism and the arguments are /online /import-defaultappassociations:”\\server\share\DefaultAssociations.xml”
This is just a bandaid until I get with Microsoft Support for more info on this issue.
When things stop working, you fix them.
Citrix VDA to client redirection is an amazing feature. Especially for high graphic, or local device interacting websites. Maintain a list of URLs, and when people hit that URL inside of any Citrix App and it sends that site to whatever the user’s default browser is on their machine. Think sites like Youtube. Hosted training. Telemedicine video portals. All sites that will perform better over the internet from the end-users browser, then it would be re-rendered inside a Citrix session. A solution that worked perfectly.
Until Microsoft Edge came to be.
Now, this is not a browser shaming post. Microsoft Edge is a great browser. However, it tries a little too hard to be your default for everything. And that is the problem.
See, in order to get VDA to client redirection to work properly in your environment, as we detail later, you need to create some Default Associations for when users get new profiles, or with mandatory profiles, every time they login. And according to the Citrix documentation, and everything that would work up until recently, was handled with the following 2 lines.
<Association Identifier="http" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="https" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />What we were now experiencing, is that occasionally this would work, but more frequently it wouldn’t. It took a lot of testing and research to find out why. Luckily there is an Application Event Log that helped find the answer.
Under Application and Services Logs there is a log specifically for Default Apps assignment on modern OSes. The path to it is Microsoft-Windows-Shell-Core/AppDefaults. While investigating this log, we would see the above association being set correctly. But then after this we would see another set of entries for http and https that would get reset to MSEdgeHTM. Along with 3 other entities. The messages would appear as below.
First:
AppDefault Info: SetDefault: Association=http, ProgId=ServerFTAHTML
AppDefault Info: SetDefault: Association=https, ProgId=ServerFTAHTML
Then:
AppDefault Info: SetDefault: Association=http, ProgId=MSEdgeHTM
AppDefault Info: SetDefault: Association=https, ProgId=MSEdgeHTM
AppDefault Info: SetDefault: Association=microsoft-edge, ProgId=MSEdgeHTM
AppDefault Info: SetDefault: Association=microsoft-edge-holographic, ProgId=MSEdgeHTM
AppDefault Info: SetDefault: Association=ms-xbl-3d8b930f, ProgId=MSEdgeHTMSo we can see our Default Associations are being hit, but then are being changed after the fact. And that was the issue.
Seems that when Edge was setting any of those 5 to MSEdgeHTM, it would reset ALL of them to MSEdgeHTM. So to fix it, I modified the DefaultAssociations.xml file defined via GPO to include all 5 entries detected.
<Association Identifier="http" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="https" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="microsoft-edge" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="microsoft-edge-holographic" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="ms-xbl-3d8b930f" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier=".pdf" ProgId="AcroExch.Document.DC" ApplicationName="Adobe Acrobat Reader DC" />And immediately it worked. Next time users logged in, MSEdgeHTM was no longer assigned. And looking in the Shell-Core log we no longer had double entries at login.
So this will be something we will have to monitor and maintain in the future, if Microsoft decides to to add additional default URI assignments that can trigger that rewrite all logic.
This should also work. Right?
For some environments we have subsets of users that we don’t want to send these pages locally. For instance Anonymous users, or thin client users, we may want to keep the browsers inside the published application session. Maybe for security, or to provide them that lower quality experience so they aren’t streaming the big game from YouTube while working.
For us the easy answer for this is to use WEM. We create a file type assignment inside WEM for http and https that points to MSEdgeHTM. Then I assign it to Everyone – with a filter of not Domain Users for anonymous sessions. And also would add AD Groups for Domain Users not needing redirection.. This works great, as it overrides the defaults after they login.
The question I had was, since this is working, why don’t I just use this and assign ServerFTAHTML as the default progid for users, and forego the Default Associations File.
Before Microsoft required hashes on the assigned default associations, I did this all the time, just with a registry entry instead of the newer FTA assignment function.
So I tried it.
It didn’t work.
I tried so many times. Edge worked. Chrome worked. Firefox worked. ServerFTAHTML…never would work. I saw it in the WEM logs so I know it was being applied. So I went back searching the net, and found this section of the documentation that I had missed.
So it seems this is an EXCLUSIVE list of browsers accepted, not the assumed inclusivity of this list. WEM will ONLY support these browsers. Very odd that Citrix doesn’t include their own Enterprise Browser, or their SFTA iexplore.exe. This is a significant limitation, and needs to be addressed in the next version. I will be putting in a feature request for this ASAP.
The setup, and what Citrix is missing in their guides.
File Type Association Defaults File
First create a DefaultAssociations.xml file to define what defaults you want for apps. You can copy and paste the code I use below. See also the pdf entry, this helps keep Edge from capturing that as well. Go ahead and remove that line if it isn’t needed, or add additional entries as you need for your environment.
<DefaultAssociations>
<Association Identifier="http" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="https" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="microsoft-edge" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="microsoft-edge-holographic" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier="ms-xbl-3d8b930f" ProgId="ServerFTAHTML" ApplicationName="Citrix FTA Launcher" />
<Association Identifier=".pdf" ProgId="AcroExch.Document.DC" ApplicationName="Adobe Acrobat Reader DC" />
</DefaultAssociations>Make sure to save this file onto the network under a read only location for users.
GPO to define Redirected URL List
Next create or modify a GPO that applies to the VDAs that you want to setup this redirection to use. Under Computer Configuration > Preferences > Windows Settings > Registry create a new Registry entry named ValidSites with the following configuration.
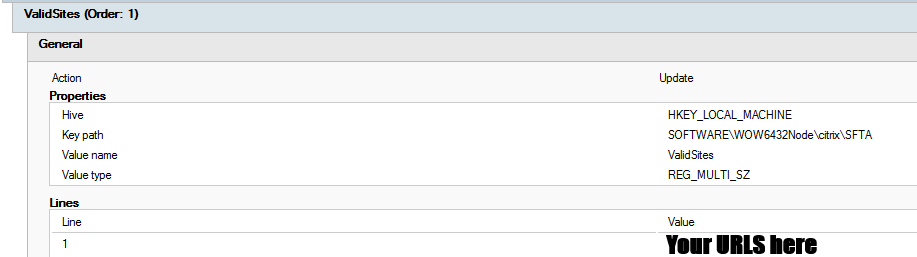
You don’t need to specify the protocol type, just the site name, and you can use the * for all children on that domain. See the following as valid examples.
*.youtube.com
portal.azure.com
*.jeffriechers.com
www.google.com
*.espn.comEnable the Citrix features in the registry
Next create the following registry entries as well in this policy. Your settings will be the same as these.
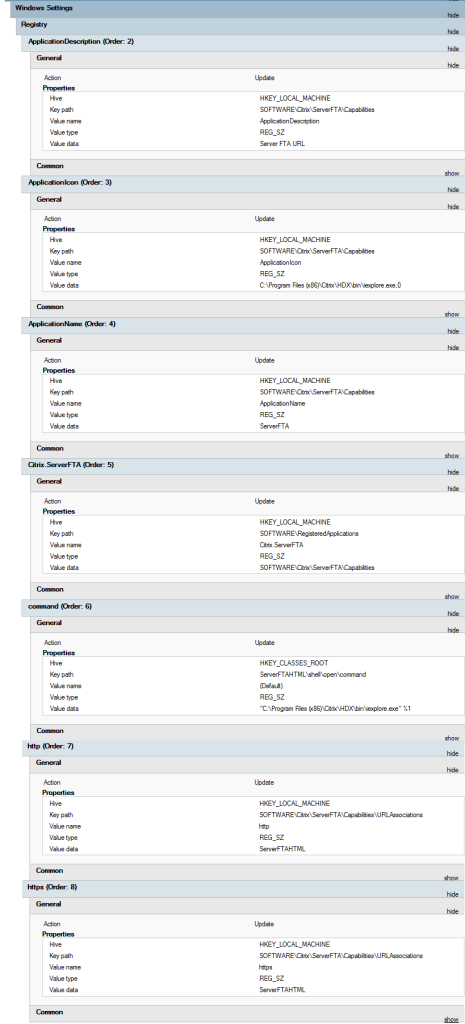
If you want to set the above settings via reg files directly in the image without using GPO, the following can be copied and pasted into a reg file to add these entries. Only do GPO, or REG file, NOT BOTH.
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\ServerFTAHTML]
[HKEY_CLASSES_ROOT\ServerFTAHTML\shell]
[HKEY_CLASSES_ROOT\ServerFTAHTML\shell\open]
[HKEY_CLASSES_ROOT\ServerFTAHTML\shell\open\command]
@="\"C:\\Program Files (x86)\\Citrix\\HDX\\bin\\iexplore.exe\" %1"
[HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\ServerFTA]
@="ServerFTA"
[HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\ServerFTA\Capabilities]
"ApplicationDescription"="Server FTA URL"
"ApplicationIcon"="C:\\Program Files (x86)\\Citrix\\HDX\\bin\\iexplore.exe,0"
"ApplicationName"="ServerFTA"
[HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\ServerFTA\Capabilities\URLAssociations]
"http"="ServerFTAHTML"
"https"="ServerFTAHTML"
"pnm"="ServerFTAHTML"
"mms"="ServerFTAHTML"
"rtsp"="ServerFTAHTML"
"rtspu"="ServerFTAHTML"
"htmlfile"="ServerFTAHTML"
[HKEY_LOCAL_MACHINE\SOFTWARE\RegisteredApplications]
"Citrix.ServerFTA"="SOFTWARE\\Citrix\\ServerFTA\\Capabilities"
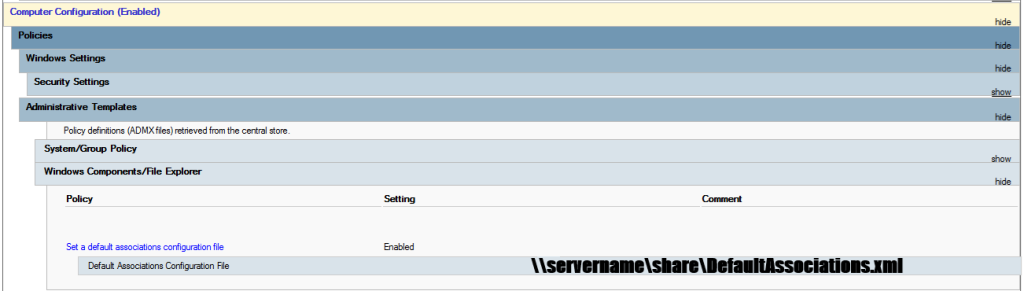
Point VDA to Default Associations File
Create or modify an existing policy, drill down to Computer Configuration > Administrative Templates > Windows Components > File Explorer and Select the Set a default associations configuration file. Enable it and point to that file on the network share. I will only set this via GPO, so we can change it globally easier. And if I used a GPO previously for the registry entries, then I will utilize that GPO instead of creating a new one.
Disable Edge Updates
To fully control Edge updates, be sure to disable all updates via GPO. And also remove the following Scheduled Tasks from the image. This should fully stop any inline updates from deploying and adding whatever function is in place to reset those default browser associations.
MicrosoftEdgeUpdateTaskMachineCore
MicrosoftEdgeUpdateTaskMachineUA
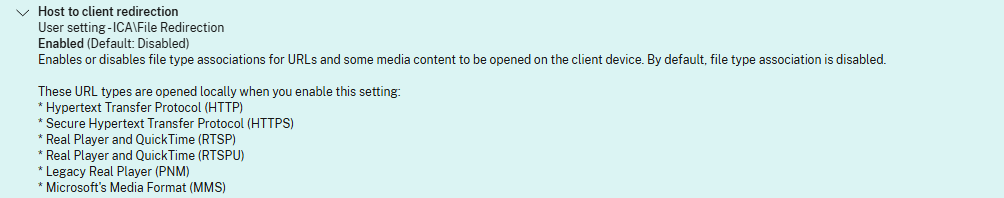
Turn on the redirection
Create or Modify a Citrix Studio Policy to enable the Host to Client Redirection under ICA > File Redirection. Make sure to assign it to the VDAs that are getting the above configuration.
Change Anonymous Users or AD Groups to MS Edge via WEM (if needed)
On the Configuration Set for your Delivery Group create a new File Type Association under Actions. Mine looks like the following.
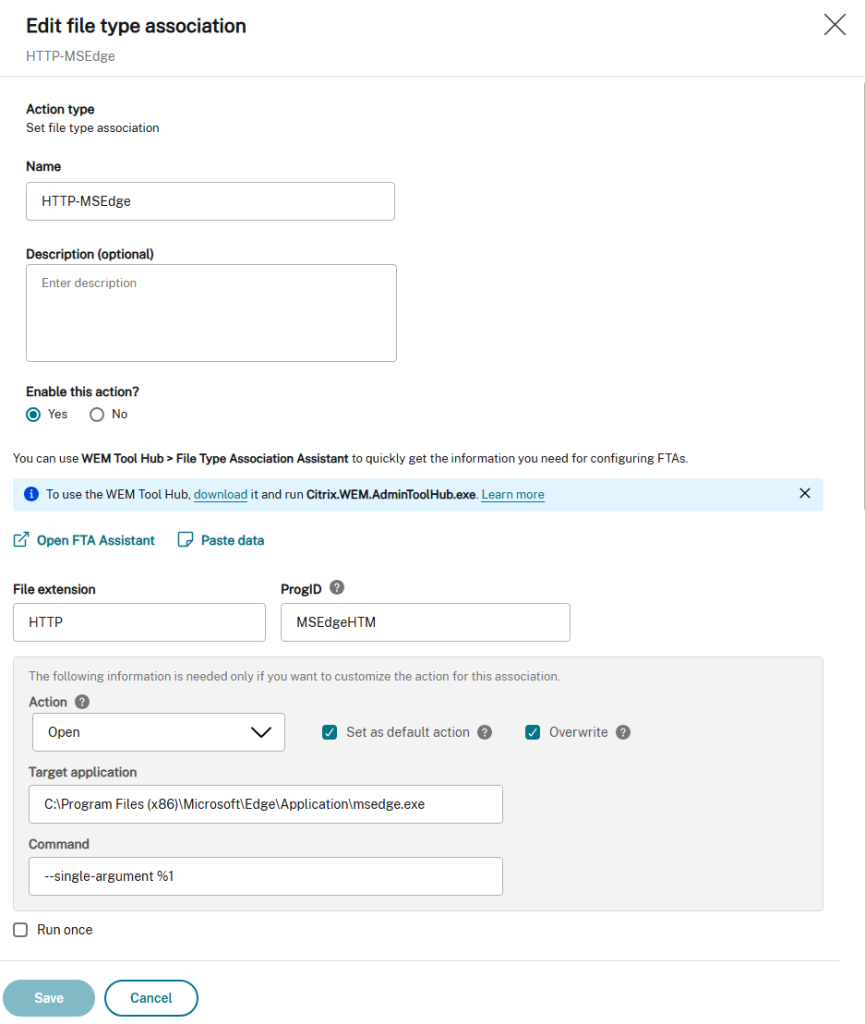
Do this again for the HTTPS file extension.
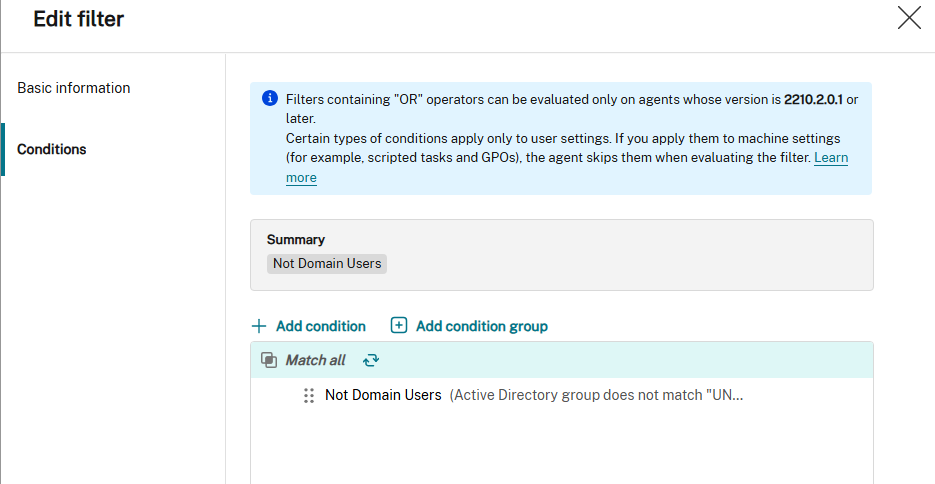
Create an Assignment Filter for Not Domain Users.
Now you can Assign those File Type Associations to Everyone with the Not Domain Users filter.
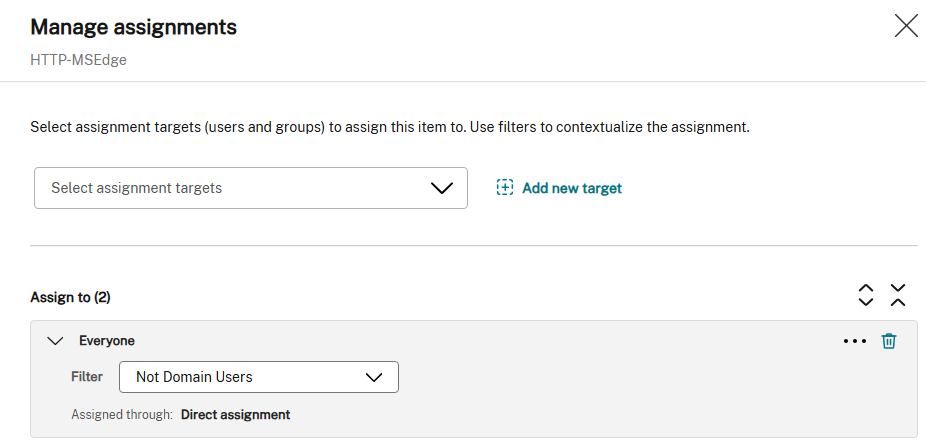
By using this assignment type Anonymous Users that are hitting this Delivery Group will get MS Edge assigned as their browser in the session.
You can also add additional Groups and Users to this policy as well, just with the Always True filter.