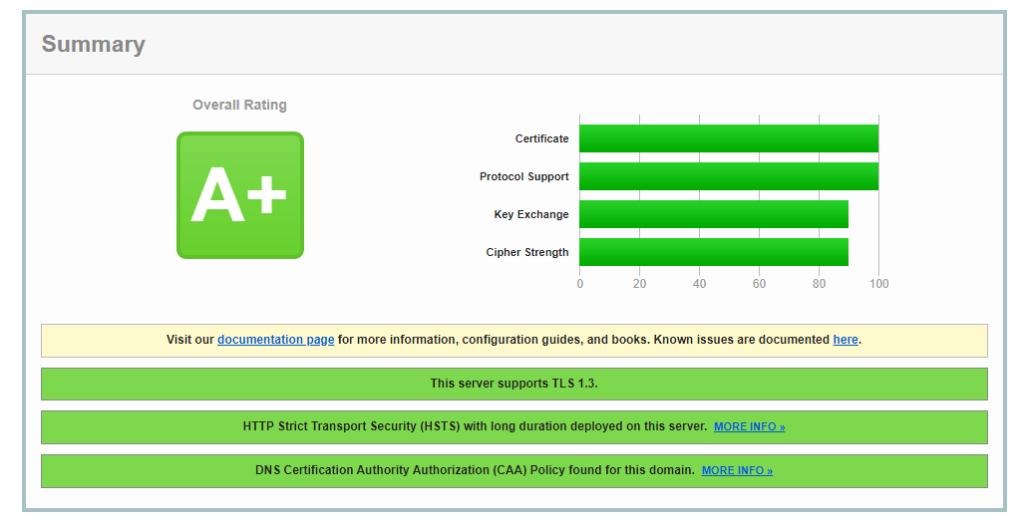
Want an easy way to get your https NetScaler sites to match my blood type? These steps should get you where you need to go. These will harden the default profile, but you could modify this in your environment to create another SSL Profile for your sites. My preferred method is to super lock down the default, and then create less secure profiles for any sites that need other security levels.
So you will want to putty into your NetScalers to copy and paste this code into the console. First, enable the default profile function. This will ask you to confirm these profile settings.
set ssl parameter -denySSLReneg NONSECURE -defaultProfile ENABLEDNext create a secure Diffie Hellman key. This process will take some time to generate.
create ssl dhparam SecureDH 2048 -gen 5Now we will create a custom Cipher Group holding only our preferred ciphers
add ssl cipher Secure_Cipher
bind ssl cipher Secure_Cipher -cipherName TLS1.3-AES256-GCM-SHA384 -cipherPriority 1
bind ssl cipher Secure_Cipher -cipherName TLS1.3-CHACHA20-POLY1305-SHA256 -cipherPriority 2
bind ssl cipher Secure_Cipher -cipherName TLS1.3-AES128-GCM-SHA256 -cipherPriority 3
bind ssl cipher Secure_Cipher -cipherName TLS1.2-ECDHE-ECDSA-AES128-GCM-SHA256 -cipherPriority 4
bind ssl cipher Secure_Cipher -cipherName TLS1.2-ECDHE-ECDSA-AES256-GCM-SHA384 -cipherPriority 5
bind ssl cipher Secure_Cipher -cipherName TLS1.2-ECDHE-RSA-AES256-GCM-SHA384 -cipherPriority 6
Next we will utilize the best ECC Curves for the updated profiles.
unbind ssl profile ns_default_ssl_profile_frontend -eccCurveName ALL
bind ssl profile ns_default_ssl_profile_frontend-eccCurveName X25519
bind ssl profile ns_default_ssl_profile_frontend -eccCurveName P256
bind ssl profile ns_default_ssl_profile_frontend-eccCurveName P384
bind ssl profile ns_default_ssl_profile_frontend -eccCurveName P521 Finally we will set our secure settings on the default profile, and remove the default settings
set ssl profile ns_default_ssl_profile_frontend -tls1 DISABLED -tls11 DISABLED -tls12 ENABLED -tls13 ENABLED -denySSLReneg NONSECURE -HSTS ENABLED -maxage 4294967294 -dh ENABLED -dhFile "/nsconfig/ssl/SecureDH" -ocspstapling ENABLED
bind ssl profile ns_default_ssl_profile_frontend -cipherName Secure_Cipher -cipherPriority 1
unbind ssl profile ns_default_ssl_profile_frontend -cipherName DEFAULTBut what if you don’t want to modify the default profile? Well you can use this same code to create a custom profile, then you can bind this profile to sites instead of the default. So if my profile was named My_Super_Secure_Profile my code would look like the following.
add ssl profile My_Super_Secure_Profile -tls1 DISABLED -tls11 DISABLED -tls12 ENABLED -tls13 ENABLED -denySSLReneg NONSECURE -HSTS ENABLED -maxage 4294967294 -dh ENABLED -dhFile "/nsconfig/ssl/SecureDH" -ocspstapling ENABLED
bind ssl profile My_Super_Secure_Profile -cipherName Secure_Cipher -cipherPriority 1
unbind ssl profile My_Super_Secure_Profile -cipherName DEFAULT
unbind ssl profile My_Super_Secure_Profile-eccCurveName ALL
bind ssl profile My_Super_Secure_Profile -eccCurveName X_25519
bind ssl profile My_Super_Secure_Profile -eccCurveName P_256
bind ssl profile My_Super_Secure_Profile -eccCurveName P_384
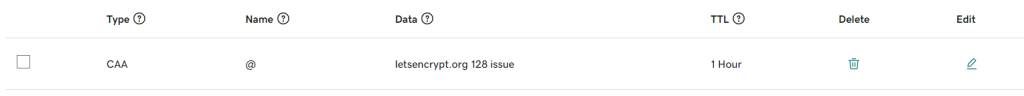
bind ssl profile My_Super_Secure_Profile -eccCurveName P_521 Now the other feature you will want to enable is DNS CAA security. This involves creating a DNS txt record in your DNS with the FQDN of the Certificate Authority. So for my let’s encrypt certs I have my Go Daddy settings as below.
Hello Jeff, thanks for the info. Do you have an updated version for 2023? Or Are these still good to use?
These should still be good to start with. I haven’t done a recent one yet for 2023 as I have been waiting for some cert vendors to roll over their new certs.